It wasn’t that long ago that SD-WAN was the next great frontier. It was the technology to displace MPLS and to give enterprise networking teams what they wanted for years – freedom from the tyranny of carriers with their overpriced capacity, long deployment times, and dysfunctional support. In short, it seemed like SD-WAN was the panacea for all that ailed IT infrastructure.
So many of my customers got drawn into comparing every little detail of the SD-WAN technology. Is packet-based or flow-based? Does it support IPv6 today (when they won’t even get to it for another year)? The list goes on.
But, like so many things, the hope of SD-WAN has given way to the reality of SD-WAN. The enterprises IT leaders I work with have learned that SD-WAN is only a piece, albeit an important piece, but still just a piece of a much larger infrastructure puzzle. Even once we’ve solved the high costs, limited bandwidth, and long-deployment times of MPLS we’re still left with numerous infrastructure challenges.
The global Internet can be very unpredictable so if you’re moving off MPLS you’ll need to think about a middle-mile provider. With Covid, we’ve seen how enterprise networking must include remote access. SD-WAN vendors have gotten better about remote access, providing mini devices for the home but that’s still the exception. Where they do offer VPN clients, users must connect back to their home office or a data center.
And, as a technology, SD-WAN lacks the full security stack needed to protect those users. For NGFW, anti-malware, URL inspection, and the like you’ll need additional products from the same or third-party vendors. That means planning for higher acquisition costs and more integration time than just purchasing and deploying the SD-WAN device.
In short, the risk with SD-WAN is the same with any new technology. Enterprises buy too much into the hype and then invest themselves diving into the details to figure which is the absolute best technology platform. But focussing on solving that one particular problem risks missing the forest-from-the-trees. We might end up with the absolutely best SD-WAN product only to realize that many other problems remain to be solved to address the full scope of challenges facing IT.
From SD-WAN to Zero Trust
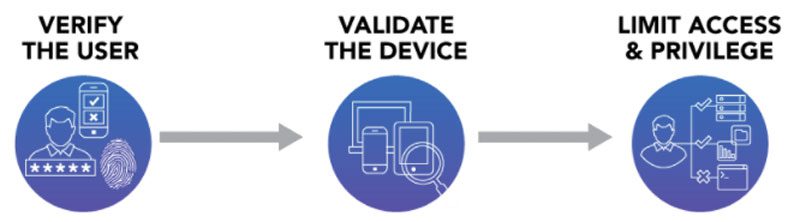
The same can be said for what’s emerging as the newest technology fad, zero-trust access. A zero-trust network is simply an architecture that restricts user access to only the necessary resources. It’s by default a “deny all” model. Resources remain inaccessible until user identity has been validated and corporate security policies have been met.
Zero trust, though, is also just another part of a much broader solution. ZT restricts resource access but you still need a wide range of other solutions to complete your security and networking picture. NGFW to inspect traffic and URL Filtering to block access to malicious sites. And, of course, networking solutions whether to provide just affordable access (DIA) or predictable long-haul performance (private backbones or MPLS).
Whether SD-WAN or Zero Trust continuing to focus on maximizing return in any one sector invariably misses the broader point: the issue isn’t whether any product set has all of the features. The question is invariably how technologies work together to solve the primary problems confronting IT.
From Zero Trust to SASE
What’s so interesting about SASE, I think, is that it reflects this change towards more strategic thinking. SASE isn’t about solving any one networking or security problem. It’s about solving all networking and security problems.
SASE offerings pull together the diverse range of networking and security technologies that IT has long used to connect and secure sites, users, and the cloud into a single, cohesive platform. So, yes, it’s important that SASE solutions tick the right boxes. There are, of course, certain macro capabilities you must have, namely SD-WAN, NGFW, analytics and a few others.
But whether you need every feature within those macro-areas is less about hitting every little tiny feature and far more about how the features work together to solve IT’s greater problems — operational efficiencies, time to respond, time to deploy, and the like.
In this, SASE represents a mental shift, one where we need to get away from comparing features, tallying them up, and seeing who has the most. It’s far more important to look at the architecture and ensure that the SASE platform can solve pressing problems of today without compromising on operational efficiency and simplicity needed for IT to scale to tomorrow. Features are something that can always be added but architecture stays — forever. (Or at least ten years, for most enterprises)